Restrict User Login for Your Application
In this scenario, you aim to enable passwordless login exclusively for specific email addresses, such as those within your company. By updating the default Presentation Definition and modifying the PEX query with a filter, you can restrict access to your application.
Before you begin
- Set up Affinidi Vault account. Follow the guide below if you haven’t set it up yet.
Get the Redirect URL of your application for OIDC. This URL is configured on your Login Configuration to receive the idToken after successful authorisation.
Optionally, install the Affinidi CLI. Follow the guide below if you haven’t installed yet.
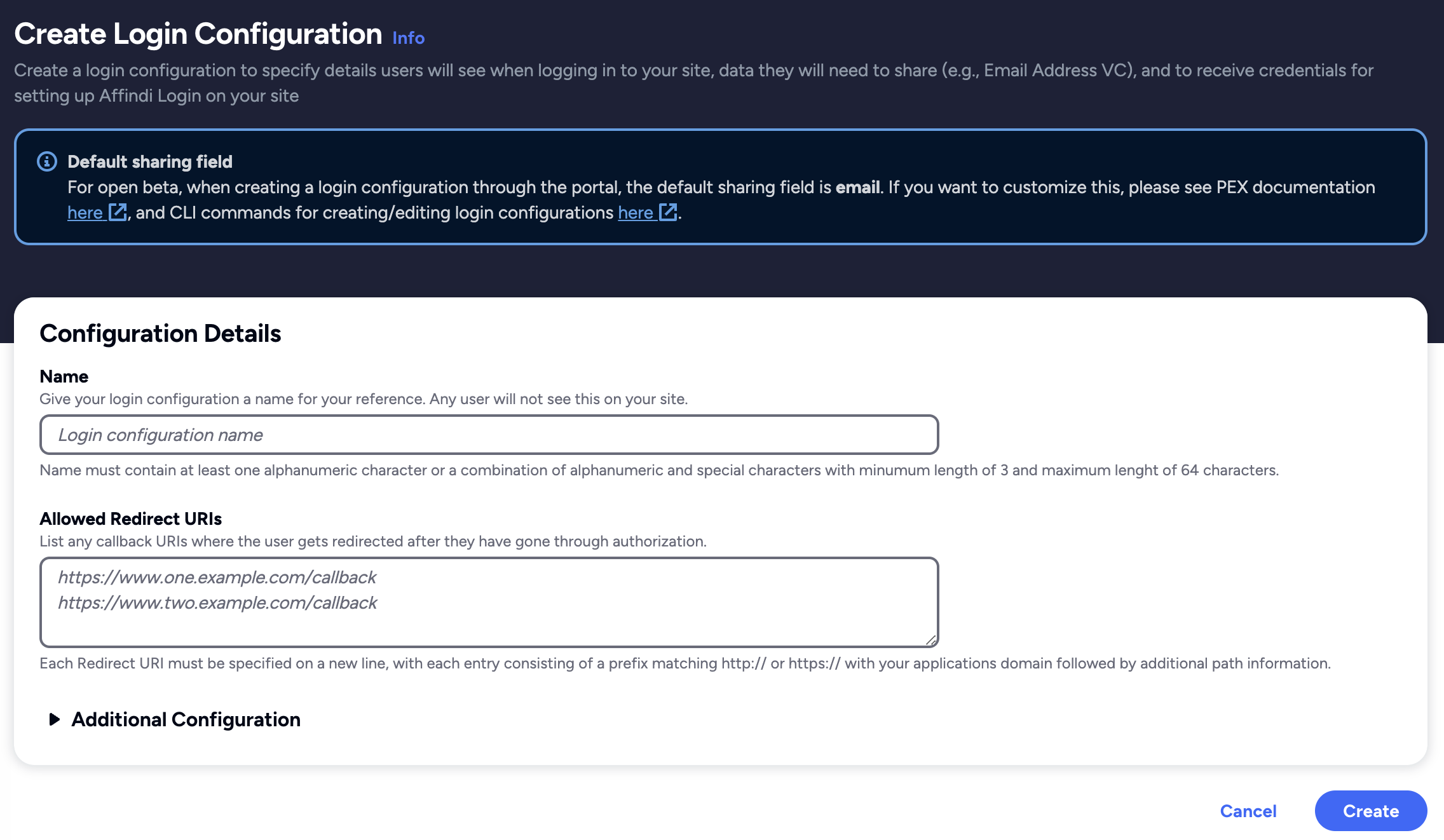
Create Login Configuration
- To create a Login Configuration, you can either use Affinidi CLI or Affinidi Portal .
Expand the section below for your preferred method:
Login Configuration uses a default Presentation Definition (presentationDefinition) and ID Token Mapping (idTokenMapping) to request the user’s email address during the authentication flow.
You can modify these defaults using Affinidi Portal and Affinidi CLI to have additional authentication requirements and request other data from the user. See this documentation.
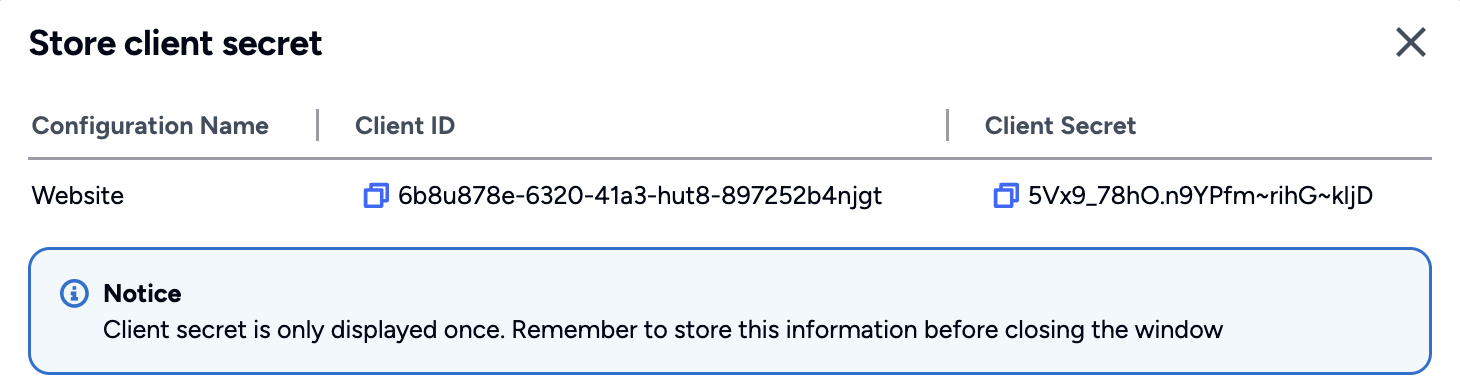
Important
Safeguard the Client ID and Client Secret diligently; you'll need them for setting up your IdP or OIDC-compliant applications. Remember, the Client Secret will be provided only once.
Update Presentation Definition
- To restrict users who can log in to your application based on the email address domain using Affinidi Login, you need to update the default presentation definition of the Login Configuration previously created and add a data filter.
{
"id": "vp_token_with_email_vc",
"input_descriptors": [
{
"id": "email_vc",
"name": "Email VC",
"purpose": "Check if data contains necessary fields",
"constraints": {
"fields": [
{
"path": [
"$.type"
],
"purpose": "Check if VC type is correct",
"filter": {
"type": "array",
"contains": {
"type": "string",
"pattern": "^Email$"
}
}
},
{
"path": [
"$.credentialSubject.email"
],
"purpose": "Check if VC contains email field",
"filter": {
"type": "string",
"pattern": ".+@companyemail.com$"
}
},
{
"path": [
"$.issuer"
],
"purpose": "Check if VC Issuer is Trusted",
"filter": {
"type": "string",
"pattern": "^did:key:zQ3shtMGCU89kb2RMknNZcYGUcHW8P6Cq3CoQyvoDs7Qqh33N"
}
}
]
}
}
]
}Based on the above Presentation Definition, we have added a filter only to accept email addresses from specific domains when authenticating users.
To update the Presentation Definition, you can either use Affinidi Portal to edit the Login Configuration using the PEX query editor found in the Additional Configuration section or use Affinidi CLI using the following command:
affinidi login update-config \
--id=<LOGIN_CONFIG_ID> \
--file=<JSON_PAYLOAD>Copy the JSON payload above and replace the email address pattern where you want to restrict the login.
See this documentation to learn more about modifying the Presentation Definition to define additional user requirements.
Set up Your Application
- Go to your application’s OIDC settings and configure the following details to integrate Affinidi Login into your application’s login flow:
{
"clientId": "<AUTH.CLIENT_ID>",
"clientSecret": "<AUTH.CLIENT_SECRET>",
"scope": "openid offline_access",
"authorizationUrl": "<AUTH.ISSUER>/oauth2/auth",
"tokenUrl": "<AUTH.ISSUER>/oauth2/token"
}If you are using libraries or plugins to enable OIDC flow on your application, please refer to their documentation on configuring these details and allowing OIDC login.
Once you have completed the set-up of your application with client credentials and enabled the Affinidi Login, only users with an email address domain that matches the pattern defined in the Presentation Definition from their Affinidi Vault are allowed to log in.
What’s next
Glad to hear it! Please tell us how we can improve more.
Sorry to hear that. Please tell us how we can improve.
Thank you for sharing your feedback so we can improve your experience.